Hierarchical Systems for Cybersecurity
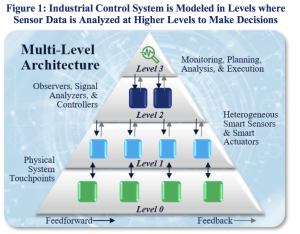 We envision hierarchical architectures for robust anomaly detection and operation resilience in cyber-physical systems. The approach to robust sensing and control as a modification of a traditional control system is illustrated in Figure 1. The multi-level architecture presents a hierarchical sensing and decision loop. The feedback path integrates data from heterogeneous sensors (Level 1) into local information from logic units (Level 2) and, furthermore, into global state awareness from assessment units (Level 3). The feedforward path evaluates actionable information and plans a new global configuration, which is distributed to logic units and, eventually, converted to action by effectors. The goal of the algorithmic logic of the feedforward path is to mitigate the impact of a cyberattack. The logic units at mid-level rely on consensus when aggregating data or executing a reconfiguration plan; thus, they form a resilient group, given that an attack can target any mid-level logic units or, worse, elements of the decision level above. We have implemented such an architecture in collaboration with the US Naval Academy with funding from the Office of Naval Research (ONR), and have published this research in several top quality control systems and security papers/venues.
We envision hierarchical architectures for robust anomaly detection and operation resilience in cyber-physical systems. The approach to robust sensing and control as a modification of a traditional control system is illustrated in Figure 1. The multi-level architecture presents a hierarchical sensing and decision loop. The feedback path integrates data from heterogeneous sensors (Level 1) into local information from logic units (Level 2) and, furthermore, into global state awareness from assessment units (Level 3). The feedforward path evaluates actionable information and plans a new global configuration, which is distributed to logic units and, eventually, converted to action by effectors. The goal of the algorithmic logic of the feedforward path is to mitigate the impact of a cyberattack. The logic units at mid-level rely on consensus when aggregating data or executing a reconfiguration plan; thus, they form a resilient group, given that an attack can target any mid-level logic units or, worse, elements of the decision level above. We have implemented such an architecture in collaboration with the US Naval Academy with funding from the Office of Naval Research (ONR), and have published this research in several top quality control systems and security papers/venues.
Reverse Engineering Code to Determine Code Mangling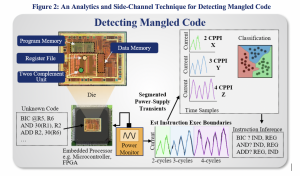
With software bill of materials being advocated by the Cyber Supply Chain Management and Transparency Act of 2014, different components of a software system or tool needs to be tested for vulnerabilities and backdoors. The state-of-the-art techniques focuses on formal verification techniques applied to source code. However, it may not be feasible in many cases to get access to source code. In our solution, power-supply side-channel leakage is observed via the power pin on the microcontroller. We create power templates representing instructions. A dynamic programming technique is used to match the templates to power-supply leakage observations corresponding to the code sequence being executed on the microcontroller, illustrated in Figure 2. Once we determine the instruction execution boundaries, we perform a hardware-based classification of the observed instructions. Using this technique, the operation code running on the device can be checked for authenticity. We have submitted the first paper that performs this analysis with sensitivity and specificity of > 99% .